The end of dodgy https certificates?
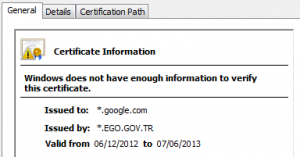
Back in January I posted about the threat to HTTPS encryption posed by regimes who “own” both a telco and a trusted CA and are therefore theoretically able to generate secret certificates which allow them to mount country-scale man in the middle attacks to snoop on secure web communication.
Since then, there have been more signs of this approach when a security researcher was openly contacted by a telco with a request to help build them a MITM infrastructure. During their pitch to him they apparently explicitly discussed compelling a local CA to issue fake certificates that would facilitate their activities.
Key to defeating this threat is in auditing the activities of the CAs to ensure that these secret security busting certificates can’t exist. A once every few years check-box audit by a firm of management consultants is no match for a state intelligence agency, so a more transparent approach is needed and here it is.
RFC6962 is an experimental standard which envisages that CAs will publish certificates that they issue to a public log. If the signing authority for the certificate that my browser has been offered also adds signed proof that it has been submitted to one or more public logs then I can assume that all is above board and the site is safe. The fact that the log is public for anyone to audit ensures that fake certificates issued by the CA will quickly be found out and make this approach impossible. Of course if ElboniaTrustTM signs a certificate but omits proof that it has been logged then my browser will be able to draw certain conclusions!
It is probably wise not to get too excited at this point as this is an experimental rather than a standards track RFC. There is nothing that says CAs or browsers have to use the mechanisms proposed. It does however offer a decent hope of solving the rogue CA problem. Certainly I’ll be making choices about the CAs and browsers that I use based on their implementing this kind of technology in future.